WiFi
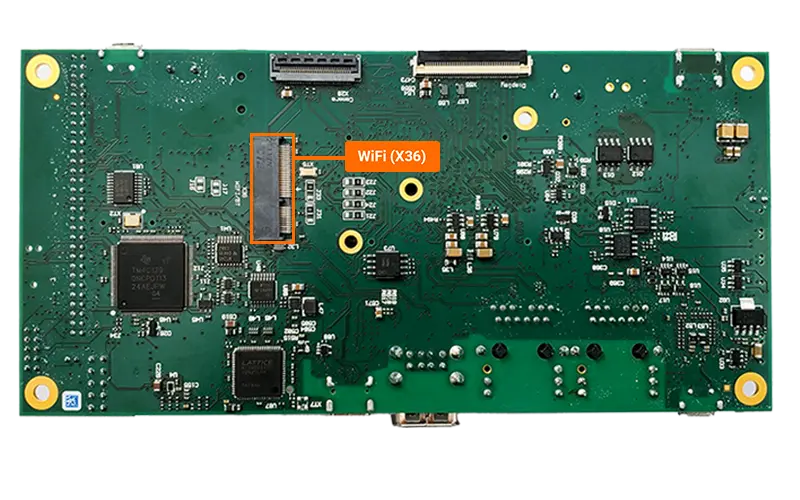
The phyBOARD-Lyra AM62x supports external WiFi modules via the M.2 connector located on the bottom of the development kit carrier board, at X36. For more information on the M.2 connector on the phyCORE-AM62x development kit, please see the Hardware Manual.
Requirements
M2 4MM Bolt (Optional)
Warning
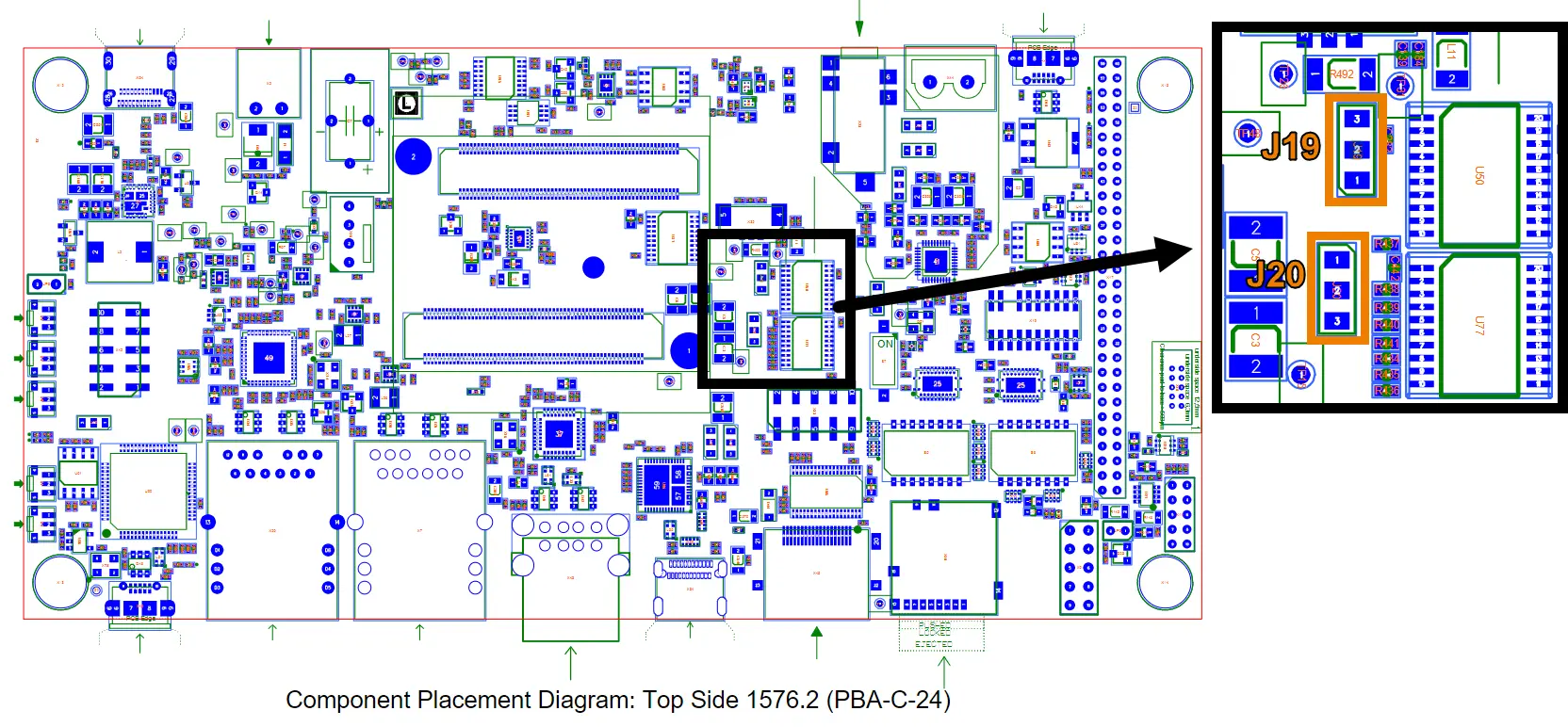
Depending on the WIFI module you are using, the jumpers J19 and J20 may require adjustment to level shift the signals routed out of the M.2 connector.
The module requires a 1.8V operating voltage, thus this module specifically requires J19 and J20 set to the 1+2 jumper position. This is the default position on the kit. (reference development kit schematics for clarification).
J19 |
1+2 = 1.8V |
2+3 = 3.3V |
Level shifts UART (Bluetooth) and PCM (audio) signals |
|---|---|---|---|
J20 |
1+2 = 1.8V |
2+3 = 3.3V |
Level shifts MMC (WIFI) signals |
Hardware Setup
Power off the development kit and disconnect the power supply.
Prepare the M.2 WiFi module by securing the antenna.
Connect the M.2 WiFi module to the X36 M.2 connector on the bottom side of the carrier board. We recommend securing the module with a M2 bolt into the soldered standoff.
Enable the Bootloader Overlay
Power on the development kit and hit any key to stop in U-Boot.
sh-uboot=> setenv overlays k3-am62-phyboard-lyra-m2-cc3351.dtbo sh-uboot=> boot
Note
For more information about overlays see the guide Configuring the Bootloader.
Configure WiFi Credentials
Once in Linux, scan for available networks:
sh-phyboard-lyra-am62xx-3:~# iw wlan0 scan | grep SSID SSID: OFFICE-GUEST SSID: OFFICE-5G
With a network identified, use wpa_passphrase to create the NETWORK section of your wpa_supplicant-wlan0.conf file with your network credentials and password filled in:
Note
Update “MYSSID” and “passphrase” to the correct credentials for your target network.
sh-phyboard-lyra-am62xx-3:~# mkdir -p /etc/wpa_supplicant sh-phyboard-lyra-am62xx-3:~# wpa_passphrase MYSSID passphrase > /etc/wpa_supplicant/wpa_supplicant-wlan0.conf
Now we can edit the wpa_supplicant-wlan0.conf to include the rest of our network configuration.
sh-phyboard-lyra-am62xx-3:~# vi /etc/wpa_supplicant/wpa_supplicant-wlan0.conf
# Giving configuration update rights to wpa_cli ctrl_interface=/var/run/wpa_supplicant ctrl_interface_group=0 update_config=1 # AP scanning ap_scan=1 # ISO/IEC alpha2 country code in which the device is operating country=US # network section generated by wpa_passphrase network={ ssid="OFFICE-GUEST" #psk="123456" psk=59e0d07fa4c7741797a4e394f38a5c321e3bed51d54ad5fcbd3f84bc7415d73d }
Establish A Connection
Enable the wpa_service for the wlan0 interface:
sh-phyboard-lyra-am62xx-3:~# systemctl enable wpa_supplicant@wlan0.service
Restart the systemd-networkd and wpa_supplicant services:
sh-phyboard-lyra-am62xx-3:~# systemctl restart systemd-networkd.service sh-phyboard-lyra-am62xx-3:~# systemctl restart wpa_supplicant@wlan0.service
Confirm wlan0 is connected to the network.
sh-phyboard-lyra-am62xx-3:~# iw dev wlan0 link Connected to 6e:d7:9a:cd:92:e9 (on wlan0) SSID: OFFICE-GUEST freq: 2437 RX: 3684015 bytes (18198 packets) TX: 57638 bytes (745 packets) signal: -88 dBm rx bitrate: 39.0 MBit/s tx bitrate: 6.0 MBit/s bss flags: short-preamble short-slot-time dtim period: 1 beacon int: 100
Check the IP address:
sh-phyboard-lyra-am62xx-3:~# ip addr show wlan0 5: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether c0:ee:40:84:4e:ec brd ff:ff:ff:ff:ff:ff inet 100.55.50.55/24 metric 1024 brd 100.55.50.255 scope global dynamic wlan0 valid_lft 70512sec preferred_lft 70512sec inet6 fe80::c2ee:40ff:fe84:4eec/64 scope link valid_lft forever preferred_lft forever
In the above example output we can see that this system has been assigned the 100.55.50.55 IPv4 address.
Verify that the M.2 WiFi module is connected to the network.
sh-phyboard-lyra-am62xx-3:~# ping -c 5 -I wlan0 google.com PING google.com (142.251.33.110): 56 data bytes 64 bytes from 142.251.33.110: seq=0 ttl=56 time=464.257 ms 64 bytes from 142.251.33.110: seq=1 ttl=56 time=13.316 ms 64 bytes from 142.251.33.110: seq=2 ttl=56 time=15.097 ms 64 bytes from 142.251.33.110: seq=3 ttl=56 time=13.265 ms 64 bytes from 142.251.33.110: seq=4 ttl=56 time=13.039 ms --- google.com ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max = 13.039/103.794/464.257 ms